Burp Suite Professional extensions we love in our pentests
Just after Portswigger released the new 2023 roadmap for Burp Suite and the exciting news of HTTP/2 support, we want to share with you our favorite extensions, that help us in our everyday job.
Detection (basic)
ActiveScan++
Performs additional checks during the scanning. Reports issues directly as normal scanner issues. No adjustable settings.
Usage: run an active scan and the plugin checks will be performed in addition to the normal checks.
J2EEScan
Performs additional Java environment related checks during the scanning. Reports issues directly as normal scanner issues. No adjustable settings.
Usage: run an active scan and plugin checks will be performed in addition to normal checks.
Command Injection Attacker
Performs a set of command injection checks during the scanning. Reports issues directly as normal scanner issues. Has a separate tab SHELLING in UI with settings.
Important note: detection by default is based on Burp Collaborator DNS requests. If the scan is performed within an isolated environment – it is better to change the Feedback channel to time delay:
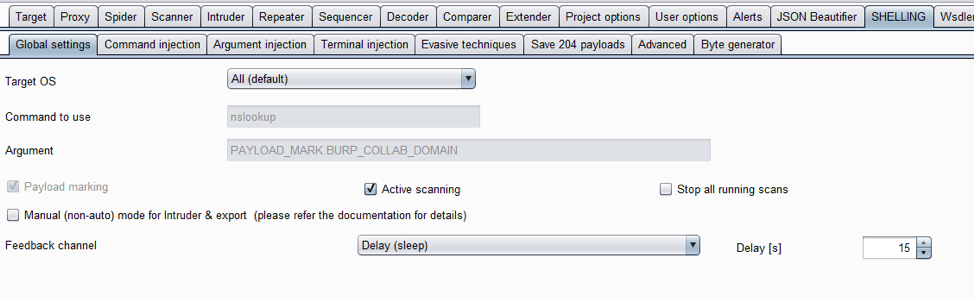
Keep the delay value based on the stability of the application response – it might cause more false positives if the delay is too small and the application response timeout is significant. Normally, 15s is OK.
Explore the settings tabs to configure additional checks, if required (please note that enabling some additional checks can significantly increase the scanning time).
Usage: run an active scan and plugin checks will be performed in addition to normal checks.
Upload Scanner
Performs a set of checks on the file upload request. Reports issues directly as normal scanner issues. Has a separate tab Upload Scanner in the UI with settings. Explore the UI settings tab to configure additional checks, if required. Please note that enabling this plugin can significantly increase the scanning time for file upload requests.
Usage: run an active scan and plugin checks will be performed in addition to normal checks.
Detection (Advanced)
Backslash Powered Scanner
Performs additional checks during the scanning. Reports issues directly as normal scanner issues. Has a separate menu section Backslash in UI with settings.
Comprehensive scan settings:
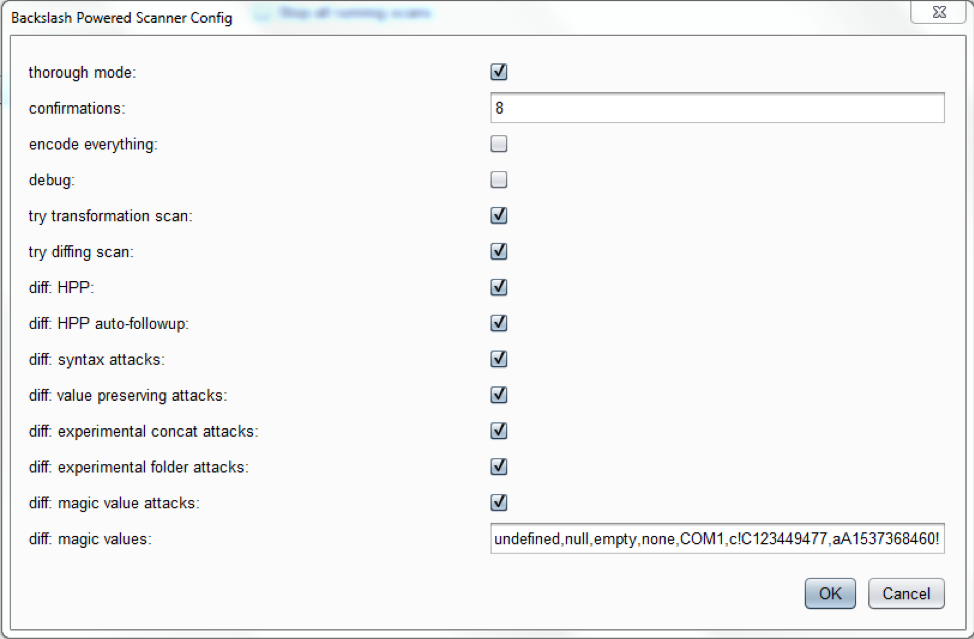
Usage: run an active scan and plugin checks will be performed in addition to normal checks.
Post-Exploitation: please note that this scanner often reveals only the possibility to reproduce some input validation issue, the exact impact should be checked with the investigation of the finding revealed by this scanner.
For example, if possible string concatenation is revealed, it requires to check if this can be
SQL/NoSQL injection, regex-based issue, formula injection or any other exploitable vulnerability.This scanner also can cause false-positives so consider the context of input (for example, nested JSON in url-encoded parameter can cause false positive JSON injection finding).
Param Miner
Performs on-demand hidden input flows discovery – such as
GET/POST/JSON parameters, HTTP headers and cookie values. Uses relatively effective binary search algorithm for the processed input detection. Reports discovered inputs directly as normal scanner issues. Has a separate menu section Param Miner in UI with settings.Scan settings:
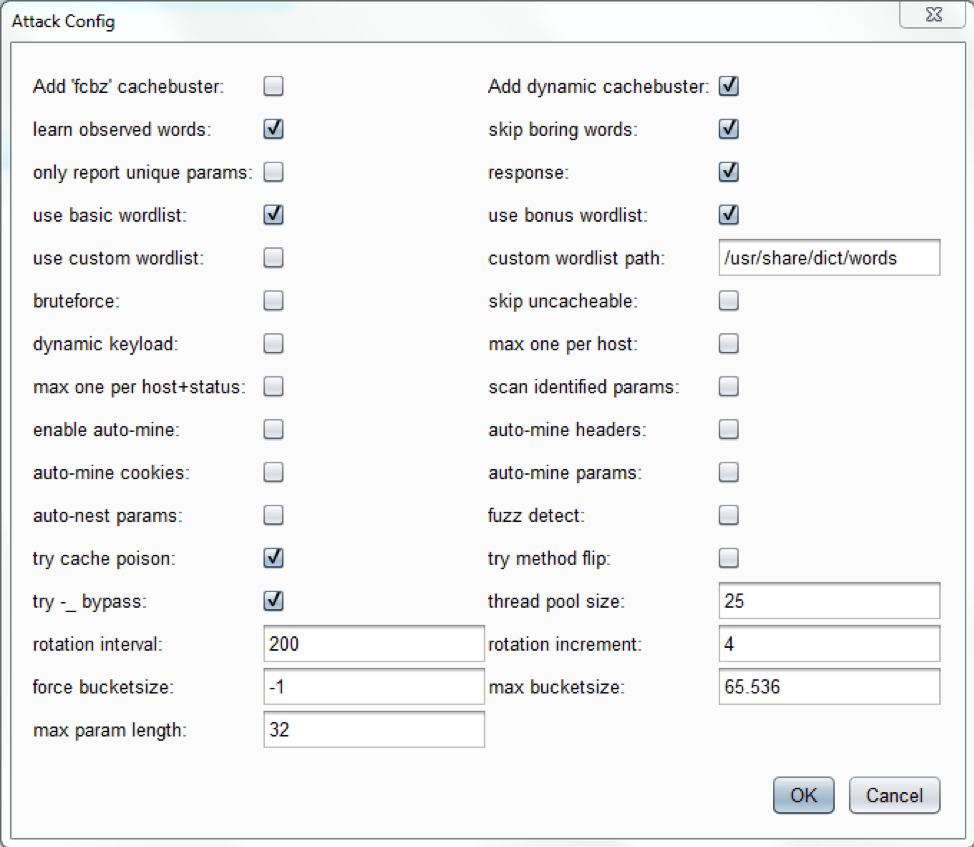
It is possible to use custom parameter wordlists and bruteforce mode.
Note
do not enable auto-mine if not required, since it will try to mine parameters for every request.
Usage: select the request to investigate and select a required input flow discovery method from the right-click menu:
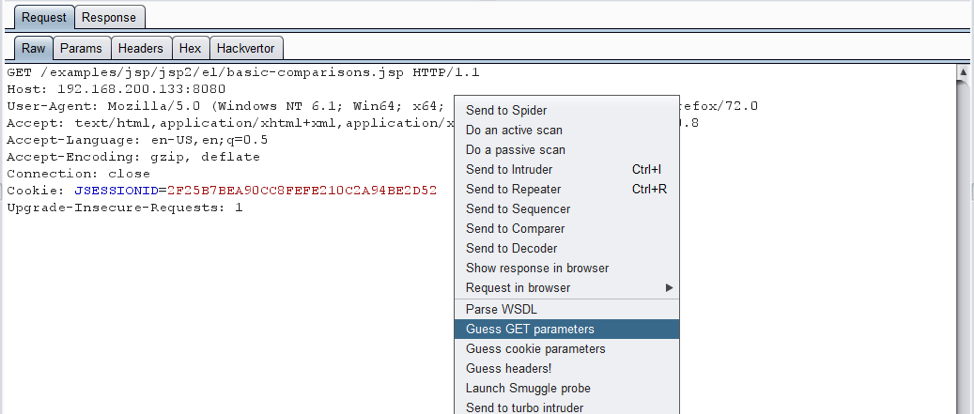
The discovery status can be checked in the Extender output window for this extension.
HTTP Request Smuggler
Performs on-demand specific checks against HTTP Request Smuggling possibilities. Reports discovered inputs directly as normal scanner issues.
Scan settings will appear when the on-demand run is selected:
Usage: select POST data-based request (POST/PUT/PATCH/etc) to run the scan from the right-click menu:
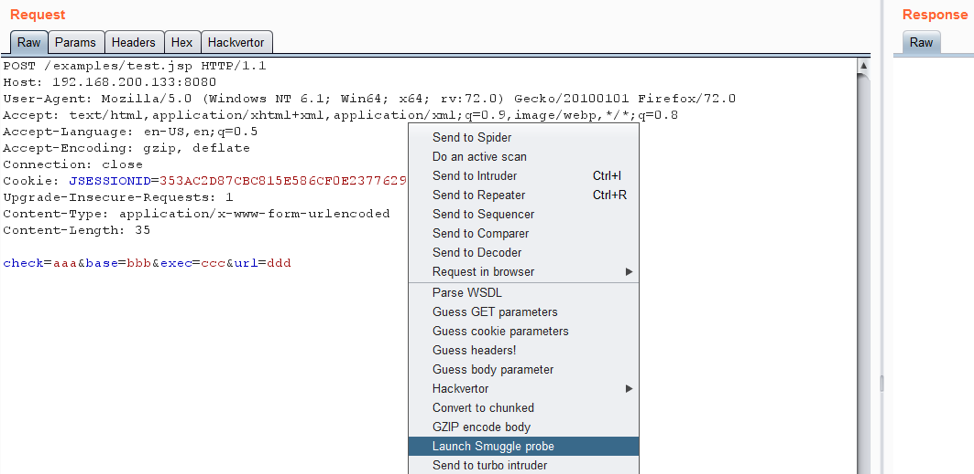
Select required checks from the settings windows and start the scan.
Post-Exploitation: please note that this scanner often reveals only the possibility to perform HTTP Request Smuggling attack, the exact impact should be checked with the investigation of the finding revealed by this scanner.
Usability
Logger++
Logs every request made through Burp Suite (including requests performed by extensions). Has a separate tab Logger++ in UI with the interface and settings.
Supports the logs export as CSV file (tab Options -> Export -> “Save full logs as CSV (slow)”).
Wsdler
Parses WSDL files and creates prepared SOAP requests. Has a separate tab Wsdler in UI with the interface.
Run the parser through the right click on the request with WSDL file content.
JS Link Finder
Automatically parses JS files in search of additional links/endpoints in the defined application scope and adds it to the Burp Suite target mapping.
Hackvertor
Supports different types of decoding/encoding arbitrary request entities (including nested) on the fly. Has a separate tab Hackvertor in the UI with the interface and settings.
Basic usage is to select the required encoding in Hackvertor tab, copy the tag and wrap it around the required request entity. After it can be processed with Repeater, Intruder, Scanner (through insertion point scanning), etc.
Now supports even Python/JS scripting processing, which makes it very powerful encoding tool.
Python Scripter
Allows custom Python script processing for supported Burp Suite extender entities (like request/response).
Can be used if some custom request/response processing is required on the fly and it cannot be done with implemented Burp Suite tools (for example, do not set
X-Forwarded-For headers for all requests from Scanner). It uses Extender API to manipulate Burp Suite entities, so refer to API manual to discover the possible functionality.