InFlight Entertainment systems security analysis
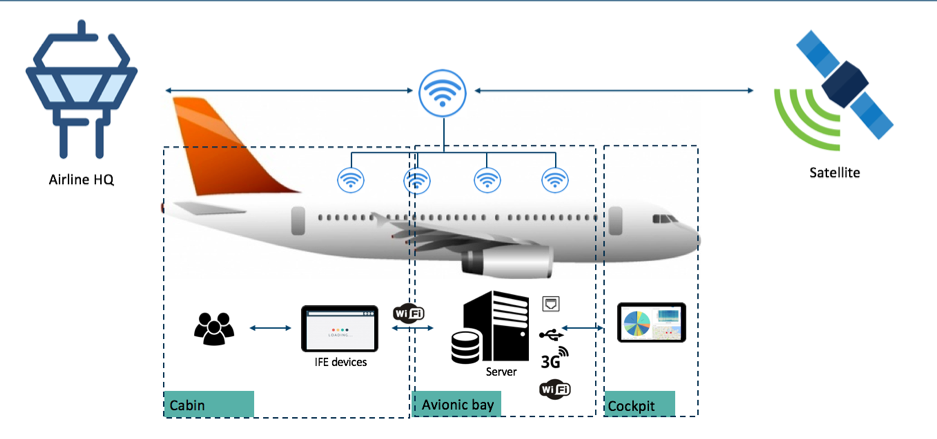
Different wireless access points are distributed in the aircraft to guarantee complete coverage to the passengers. A central server is used to distribute content and offer connection between the departments. A more detailed representation can be the following:
- Media protected by copyright
- Usernames and password of the users
- Credit cards used to purchase goods, contents or faster connections
- Personal information of the passengers
- Name
- Surname
- Date of birth
- Address
- Phone numbers
- Device in use (in case of BYOD)
- Private information shared by the passengers with the cabin crew
- Health problems
- Allergies
- Private messages shared between passengers
- Internal IPs of other devices in the aircraft
- Communication with the air traffic controllers
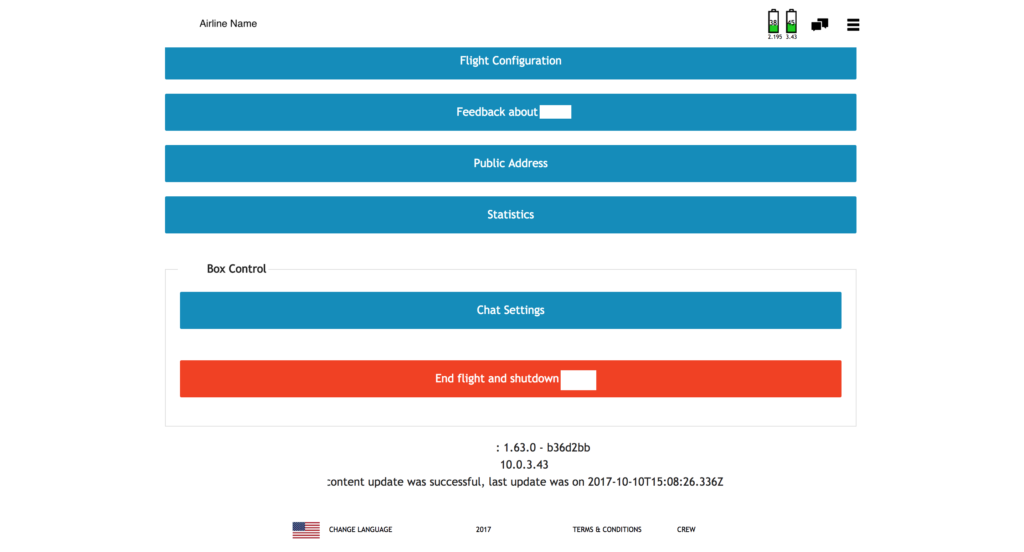
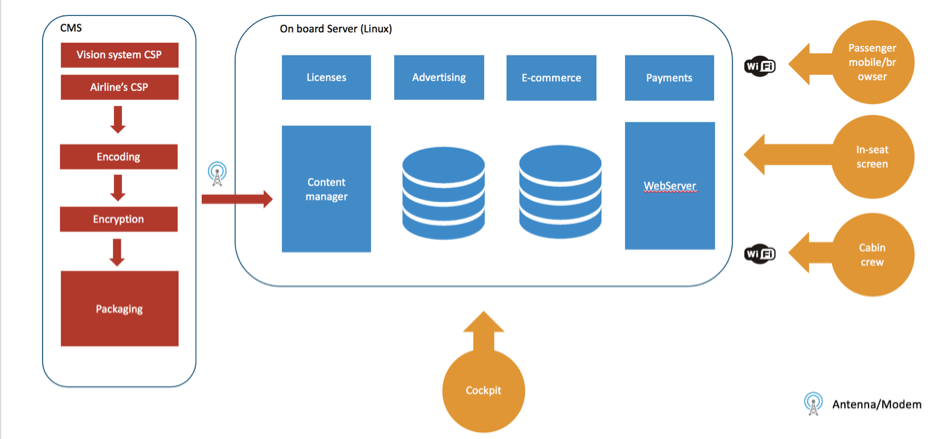
Web panel
Every IFE offers the possibility to connect your own device, such as laptops, tablets or phone, and register an account via the website deployed on the web server. The web panel is exposed to every issue that affects web applications, such as the OWASP Top 10.
Wi-Fi network
The wi-fi network allows users to connect their own devices to the network and get access to internet.
Web sockets
Web sockets are mostly used to provide real time information about the flight, status of the devices (battery level, CPU level etc)
USB port on the screen
The USB port on the seat’s screen is easily accessible by any customer on the aircraft and can be used to carry on fuzzing black-box testing.
Debug port
The debug port is used to get information about the system and /or get access to the IFE for maintenance. It is marked as low risk, because is not accessible from the screen of the passengers but it is only accessible from the IFE servers.
Web server
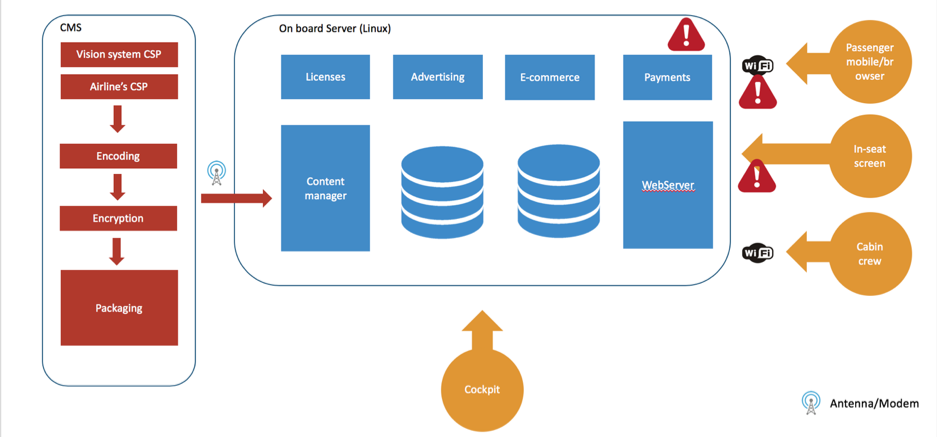
Our research shows that the top vulnerabilities that affect the web portal can be categorized as the following.
Authentication bypass
In most of the analyzed IFE systems we were able to bypass the authentication, impersonating admin users.
Cross-site scripting (stored, DOM based, reflected)
Input sanitisation is most of the time missing, and this will lead in XSS attacks.
Username disclosure through error messages
Error messages show that a particular username exists or not in the system, helping the attacker in fine tuning brute force attacks.
Unauthenticated endpoint that lead to customer info stealing
Not all the endpoints are protected from session validation checks. Many endpoints used to retrieve users’ info based on the username, were not protected and could be exploited through brute-force attacks, to retrieve info about passengers.
Escalation of privileges (from user to crew member to maintenance).
Sessions are not properly validated, relying on client side validation. Admin usernames are always available and used by maintenance or crew members with higher privileges.
Credit Card information disclosure
Credit cards stored in the system, can be used to purchase goods or internet connection. A user’s credit card could be used multiple times. Communication over websockets could leak credit card transactions. During our testing we were able to retrieve passengers’ CC information and purchase history.
User Private information disclosure (Name, surname, username, city, country, address, phone number for every passenger).
Passenger data could be retrieved without any form of authentication. Unprotected endpoint could be used to retrieve crew members and passenger’s private info.
Flight data manipulation
IFE systems offer information about the current flight, and enable the cabin crew to modify data such as:
- Departure
- Airport
- Arrival
- Airport
- Number of passengers
- Weather at destination
- Routes
Once the attacker is able to bypass authentication mechanisms and escalate his/her privileges to a cabin crew member, he/she can manipulate the data and impact the user experience, creating disorientation between passengers.
Wi-Fi network: no network isolation
Passively listening on the network, it is possible to receive and retrieve information about passengers and device installed in the aircraft
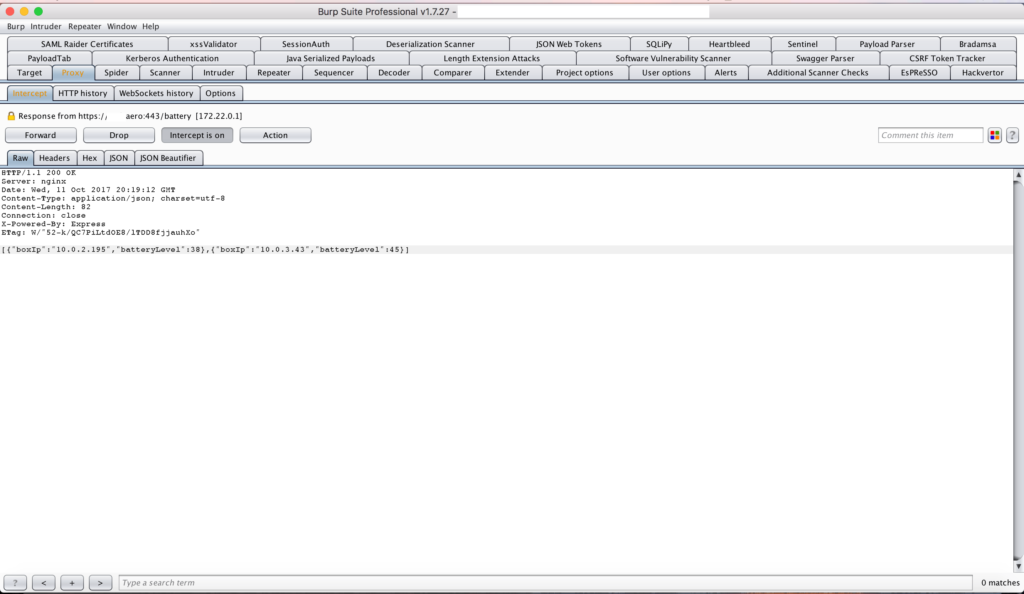
Websockets: Internal IP disclosure
The IFE systems are composed of different devices distributed around the plane. Every device communicates its status (battery level, CPU level, in use/not in use etc), as a keep-alive information. The problem is that every device communicates also its IP (ex. 10.X.X.X) and its MAC address, allowing attackers to expand their scope.
Practical examples
At DCODX we love to explore new technologies, and IFE systems are pretty interesting ones. Recently we analyzed one of the new player in the market, and discovered few vulnerabilities, such as:
- Authentication and Authorization bypass
- Passenger information stealing
- Plaintext information over the network
- Authentication and
- Authorization bypass
During our test, we were able to bypass the login panel and access the IFE as a cabin crew member, without using any stolen credential. From the panel we were able to check the status of the devices (2), check statistics and modify the information about the flight shown to the passengers. One interesting feature was the possibility to shutdown the IFE and create a DoS for every passenger.