How our training was accepted at BlackHat training EU, ASIA and US and DEF CON
In the past two years our training Hackable.sol: DeFi and Smart contract hacking got accepted at DEF CON Trainings and Black Hat trainings. It allowed me to meet amazing people from all around the world, organizers behind the most popular cybersecurity conferences while having the opportunity to travel and challenge myself to the next level. […]
Aligning Secure Coding Training with NIST 800-50r1 (CPLP)

The National Institute of Standards and Technology (NIST) has recently published the Special Publication 800-50r1, “Building a Cybersecurity and Privacy Learning Program.” This guide underscores the importance of tailoring training to diverse audiences and leveraging innovative technologies to enhance their Cybersecurity and Privacy Learning Program (CPLP). One of the cornerstone principles outlined by NIST is […]
Join us at HITB Abu Dhabi

Are you planning on joining Hack In The Box Abu Dhabi? We will be there with our training Hackable.sol: Smart contract hacking in Solidity. This is an exceptional opportunity for developers and security professionals to dive deep into the world of blockchain security. What to Expect from the Training Our training session is meticulously designed […]
DCODX and SecDim are joining forces to provide a continuous secure code learning solution

In the rapidly evolving world of software engineering, practicing the latest secure coding topics is crucial for developers. However, DCODX, a leader in developer security training, has identified a significant challenge: many developers do not practice their acquired knowledge, often waiting until their next annual training session. This leaves them unprepared for emerging security vulnerabilities […]
Assess your DevSecOps Maturity with our self-assessment
Measuring DevSecOps maturity is of fundamental importance for development teams to enhance their overall cybersecurity posture and operational efficiency. A DevSecOps maturity assessment provides valuable insights into the effectiveness of security practices integrated into the development process. By evaluating their maturity level, development teams can identify gaps, weaknesses, and areas for improvement, allowing them to […]
Burp Suite Professional extensions we love in our pentests

Just after Portswigger released the new 2023 roadmap for Burp Suite and the exciting news of HTTP/2 support, we want to share with you our favorite extensions, that help us in our everyday job. Detection (basic) ActiveScan++ Performs additional checks during the scanning. Reports issues directly as normal scanner issues. No adjustable settings.Usage: run […]
OWASP MSTG Crackme 3 writeup (Android)

The application The application has the same look as the others and the same message when root detection kicks in. Let’s have a deeper look. As usual, we extract the source code from the APK and look into interesting classes.The main structure of the app is the following ├── owasp │ └── mstg │ └── uncrackable3 […]
OWASP MSTG Crackme 2 writeup (Android)

The application To understand more about the application, we extract the source code from the APK and look into interesting classes. The structure of the app is the following: ├── owasp │ └── mstg │ └── uncrackable2 │ └── R.java └── sg └── vantagepoint ├── a │ ├── a.java │ └── b.java └── uncrackable2 ├── […]
OWASP MSTG Crackme 1 writeup (Android)

Intro The Uncrackable Apps are a collection of mobile reverse engineering challenges made available by the creator of the OWASP Mobile Security Testing Guide to practice reverse engineering skills. Our mobile security researchers had some fun cracking the apps during one of our R&D Friday afternoons. You can find more info regarding the challenges here: […]
InFlight Entertainment systems security analysis
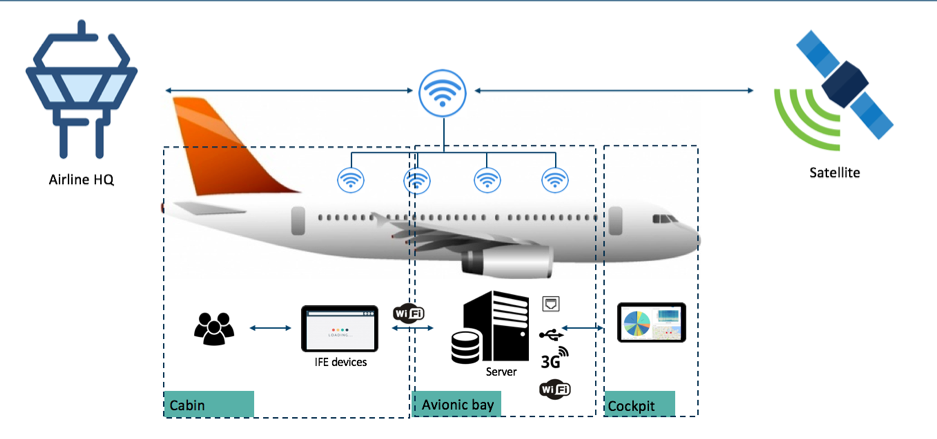
Nowadays it is becoming more and more common for airlines to adopt IFE (In Flight Entertainment)/ IFC (In Flight Connectivity) solutions to “entertain” passengers, offer free movies, music, games, information about the flights (altitude, speed, temperature outside, temperature inside etc) and also the possibility to buy products or fast internet using common payment methods such […]